Self-Service Password Reset can be attractive to customers utilizing Office 365 as it can dramatically reduce help desk calls from users who have forgotten passwords after extended holidays etc. With this users can reset their passwords much like they would for other websites such as eBay, PayPal etc.
Login to Office 365, expand Service Settings and
then Passwords. Click on Azure AD Admin Center this will forward
you to a trial subscription of Microsoft Azure, this is required as you need
access to the Azure AD Admin Center to enable Self-Service Password Resets.
Sign up for a free trial and ensure that is associated
with your Office 365 tenancy. You will need a mobile phone to confirm
you are not a robot and a valid credit card to sign up for the trial.
Click on Active Directory from the list of services and then select the Configure tab. Now click Yes from the Users Enabled for Password Reset option.
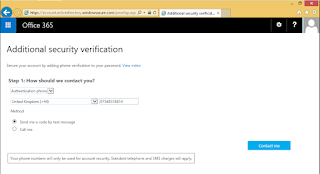
You can set the authentication method to Office Phone, Mobile Phone, Alternate E-mail Address and Security question, or a mixture of all four. I have selected Mobile Phone and Alternate E-mail Address.
The Require Users to Register When Signing into Access Panel? option ensure users are prompted to configure their password reset options the next time they login.
It is also recommended that Write Back Passwords to On-Premise Active Directory is enabled to ensure all passwords remain in-sync at all times. Click the Save button on the Azure pane.
Now if you try to login as a user, you will be prompted to configure your alternative password reset routes, click Set it up Now on each of them.
To confirm you Mobile Phone you will require a text or phone call. You will receive a code that you have to enter into the web page to confirm the mobile phone is in working order and belongs to you.
The same goes for the alternate e-mail address, if you enter your personal e-mail address in here you will receive a message from Microsoft with a code in.
Click Finish when everything has been completed.
The password reset experience is outlined below.